Home
Cyber Security Testing for Everyone
We help you find and fix your IT weaknesses before hackers exploit them.

Vulnerability Detection
We identify the vulnerabilities putting your company, your clients and your data at risk.
IT Security Consultancy
We consult on all aspects of IT Security including cybersecurity, physical IT and human aspects.
IT Security Audit
We can audit your company, its documentation and processes from a security best-practice perspective.

Act now
Don't leave it too late
Fix the weaknesses before they are found by hackers and become a business-critical issue. Data breaches and downed IT can ruin your business.
- Identify vulnerabilities
- Remediate them
We think like a hacker
We are certified ethical hackers
Who better than real hackers to find the weaknesses in your website, software and hardware? Our testers are EC-Council Certified Ethical Hackers with real-world experience.
- Certified experts
- Real-world experience

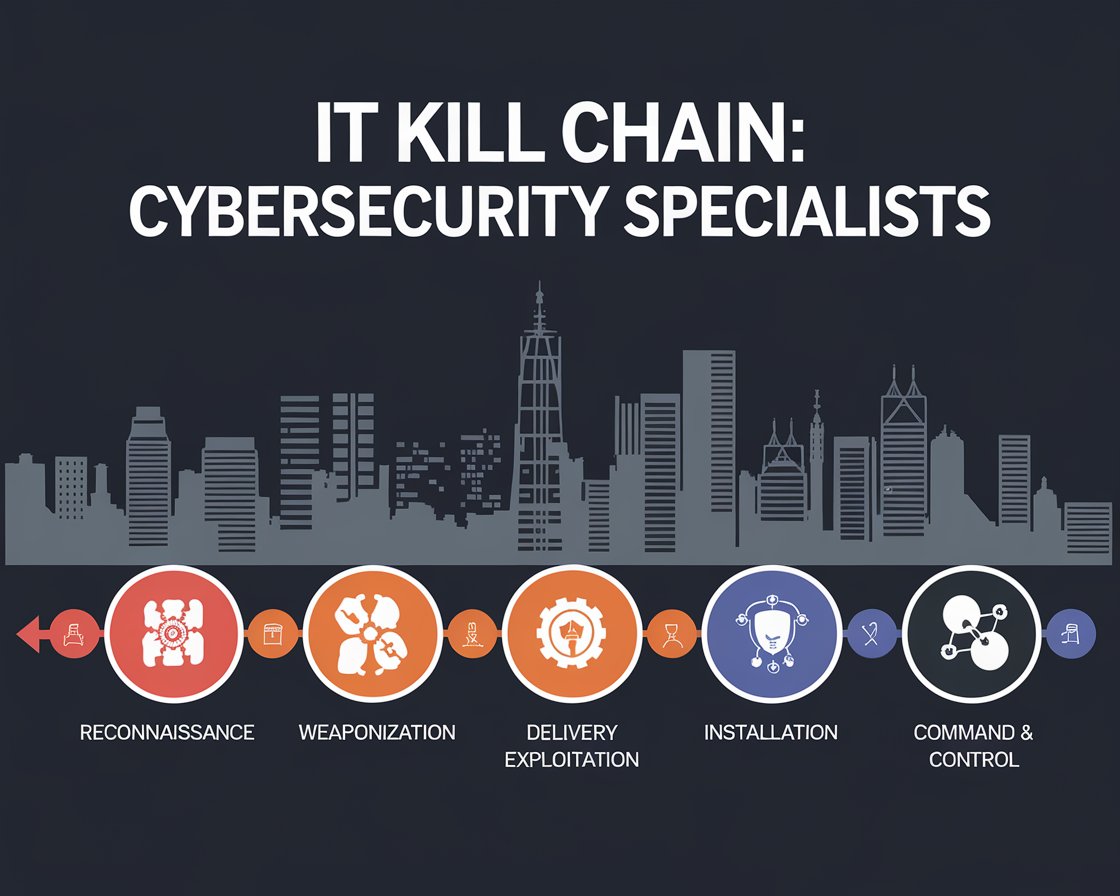
Why IT Kill CHain?
Learn about the Lockheed Martin Cyber Kill Chain®
Developed from the military Kill Chain model by Lockheed Martin in 2011, the Cyber Kill Chain outlines the various stages of common cyberattacks and, by extension, the points at which the information security team can prevent, detect or intercept attackers.
- Think like a hacker
- Stop the hacker
What we do
How we keep you protected
We have a variety of skills in the sphere of IT Security but they won't all be relevant to your business and risk profile. We can provide a service tailored to your business, budget and your biggest concerns.
Vulnerability Finding
We can Penetration Test your website and systems and identify any vulnerabilities that could be exploited.
Keep Your Data Safe
Avoid data breaches and keep your customers happy. Litigation and class action lawsuits are becoming mainstream.
Audit Your Processes
We can advise on compliance with standards such as ISO 27001 or review business processes for potential weaknesses.
Application Security
Make application security testing the norm for your business. Setup static (SAST) and dynamic (DAST) security testing.
Mobile App Testing
Test your mobile application for vulnerabilities and potential exploitation. Don't let your app endanger your data and customers.
Social Engineering
Evaluate your employees' susceptibility to exploitation. Check their online exposure or simulate real-world attacks.